Sign in with Twitter
(Part 1)
Today, many websites on the World Wide Web offer different types of authentication, using its own internal functionality or through various social networks. Often, they use different resources such as Loginza, uLogin, LoginMe and others. In this blog, I’m going to tell you how to write your own code for Twitter authorization. This blog consists of several parts that contain a description of each step of the procedure.
Recently, Twitter has tightened its security system since it came under fierce attack by hackers who gained access to its resources. Now, Twitter experts are working on a so-called two-factor identification system to verify the password. Obtaining user information requests through markers has not changed yet, so I will now explain how the process of the authorization works.
1. Site user clicks the button "login via Twitter”;
2. PHP code generates a request for a marker acquiring and sends the request to Twitter (e.g. by using PHP curl);
3. Twitter sends the request back;
4. PHP code of the site creates href based on the received request token and redirects the browser for Twitter authentication.
5. Client browser goes to Twitter. User logs in and allows or doesn't allow Twitter to use user's personal data;
6. Twitter generates a href based on completed user's actions on Twitter and callback functions, redirects the browser to your website with verification tokens. If there’s no verification token, then Twitter transmits token rejected.
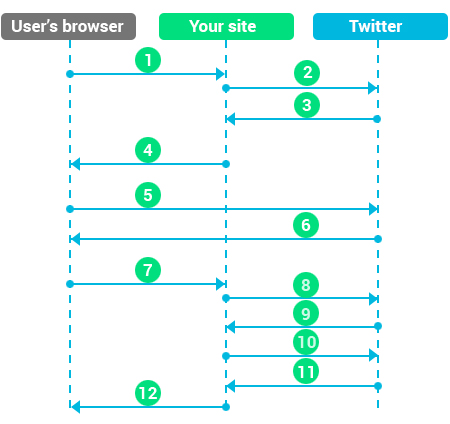
7. The browser goes on your site with appropriate markers.
8. PHP code on your site gets verification token, generates a request for token access and sends the request to Twitter (e.g. by using PHP curl);
9. Twitter gives token access back;
10. PHP code on your site generates a request for data using token access and sends the request to Twitter (e.g. by using PHP curl);
11. Twitter gives information on the given user;
12. PHP code checks your data from Twitter and from your personal database. If correct, user logs in. In case of wrong data, we turn refusal application to user's browser with an error (failure or other error that occurred during authentication) and click again to repeat the authorization.
See also: Zen Coding – the Method of Quick Coding

